MAJOR CONCEPTS IN PERMISSIONS
- Keycloak is primarily used to manage Users and Roles as well as their assignment.
- ONE Web Application - where you can assign preconfigured permissions to Users and Roles. It is also possible to change the default configuration and create custom permissions on the ONE Web Application.
- Users (Persons) - identify people or services who have access to Ataccama ONE.
- Role - the container for permissions that users can perform in ONE on entities in alignment with the company organization chart. “Role” refers to the roles defined in Keycloak, for example, MMM_ admin.
- Users need to be mapped to Roles. This will determine their node permissions based on the operations allowed for that role on individual nodes. A user can have more than one role assigned to them. Users and roles are managed primarily in the Keycloak service, then synced with ONE.
- Users and Roles access can be regulated by permissions that are configured via different blocks: Capabilities, Operation Sets, and Operations.
- Permissions of Users and Roles can be regulated by assigning and removing preconfigured Capabilities. Capability refers to composed permissions that can regulate access to multiple entity instances across a hierarchy.
- Capabilities are composed of Operation Sets and Operations.
- There are three pre-defined operation sets that determine what the user can do with the node: Owner, Viewer, and Editor. On the ONE Web Application, within entities, you can assign or add operation rights to Roles.
- When launching Ataccama ONE for the first time, there is a default configuration set, containing default Roles and first Users assigned, with their set Capabilities, Operation sets, and Operations.
You can manage access either on all entity instances on the same level or instance by instance. It is also possible to manage access across the hierarchy of entities, ie. assign a capability that will regulate access to a data source, locations, and catalog items at the same time.
USECASE:
The “data tab” in the ONE Web Application must be restricted for certain users as per the requirement. The permissions model was updated including a new operation set named Metadata viewer. Users with this role have view permissions for this data source, its metadata, connections, and credentials. Editing or running data processes is not allowed. They have no permissions for workflow transitions and no access to data samples.
STEPS TO BE FOLLOWED TO CHANGE THE PERMISSIONS MODEL IN ONE WEB APPLICATION.
- Navigate to Global Settings in the left panel of ONE Web Application
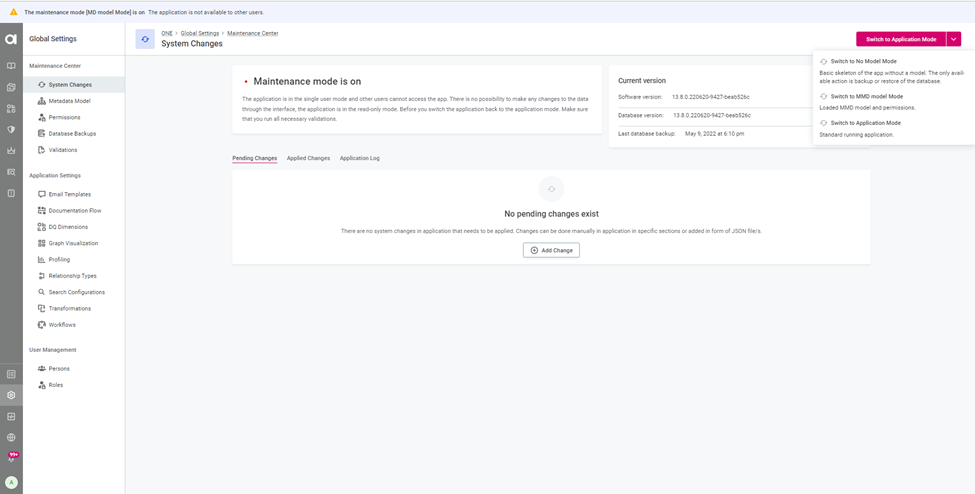
- Click on System Changes to switch to Maintenance mode
- Switch to MD model mode
- Application will switch to the Maintenance mode
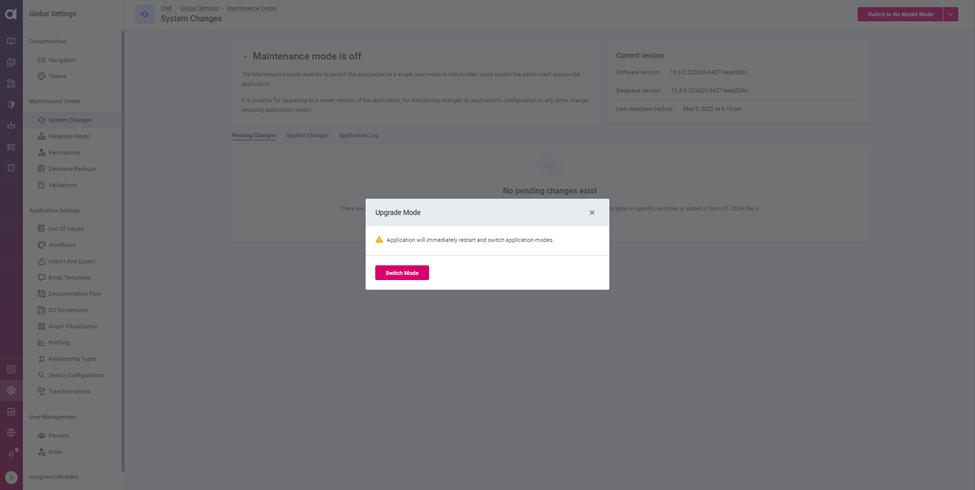
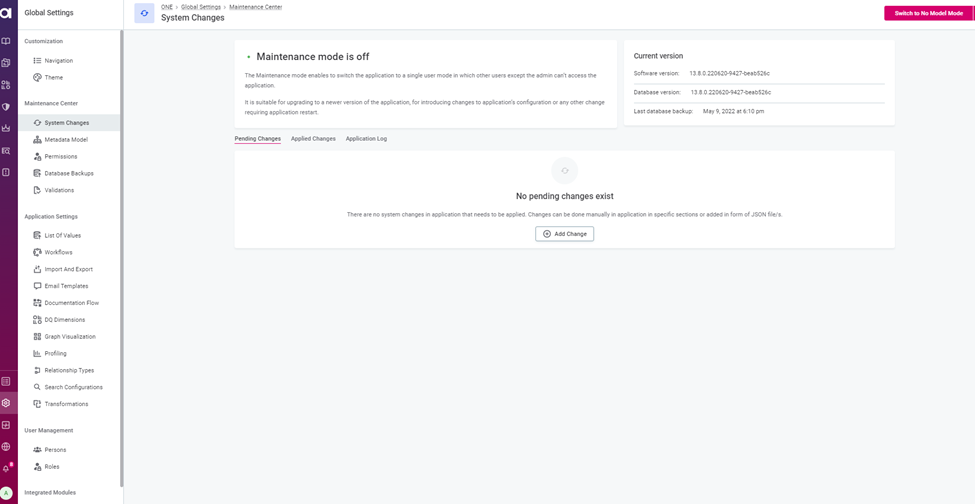
- Application will be in Maintenance mode until we switch back to the application mode after changes.
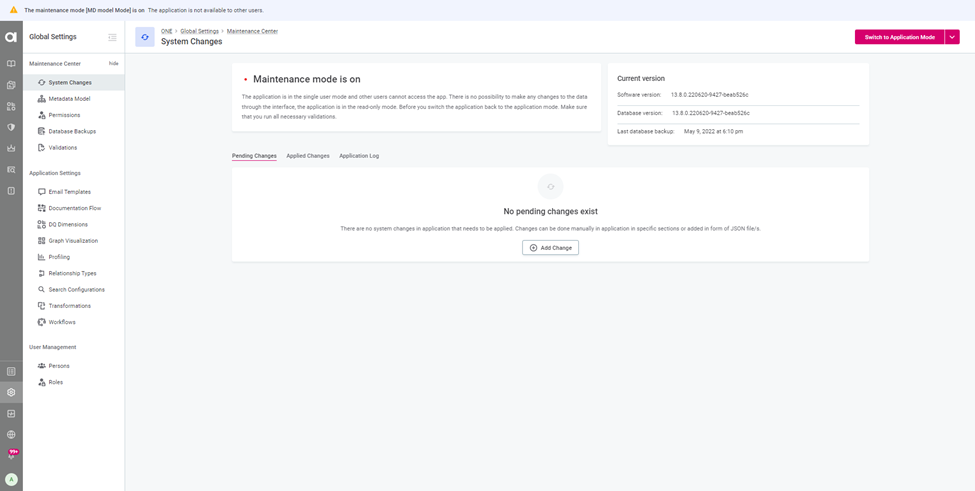
- Click on the permissions tab on the left panel
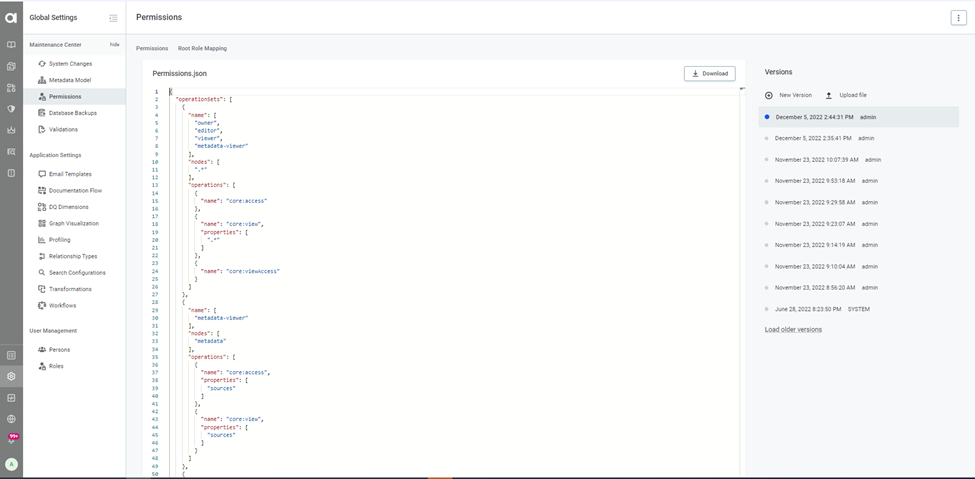
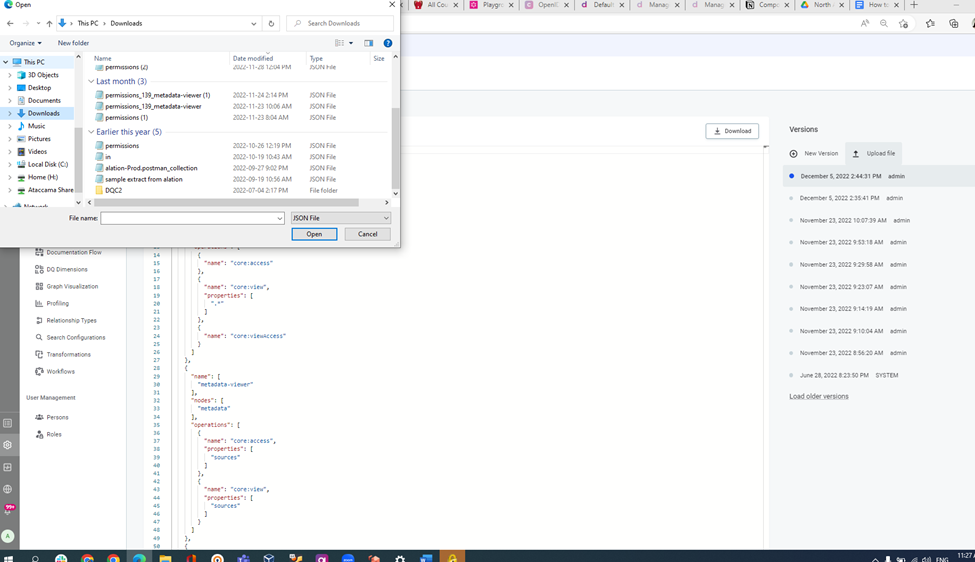
- To take a backup of the current permissions model click on the download option. The current permissions model will be downloaded.
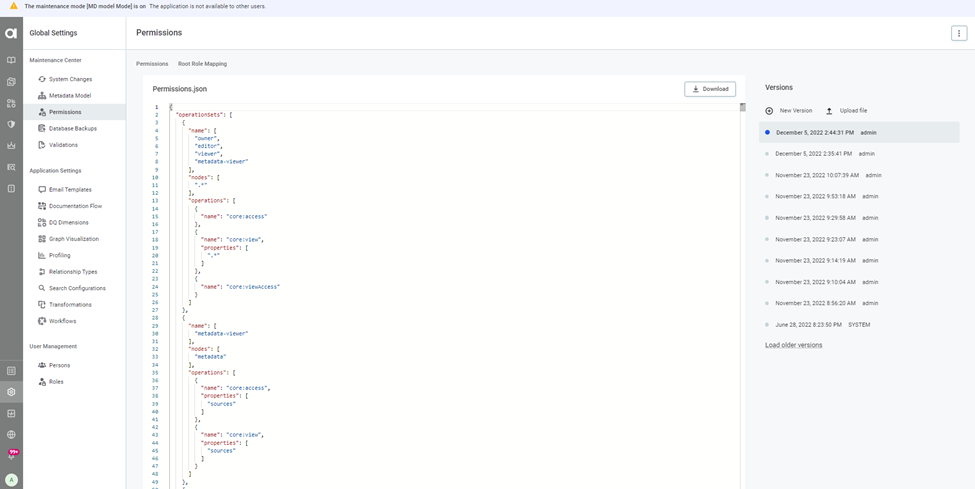
- To upload the new permissions model click the upload file option and update the new permissions.json file
- Switch back to the application mode under system changes
- Application is in the progress of switching back
- Once the system changes are updated check for the permissions restriction based on the assigned role for the user.
- In the Keycloak, choose the MMM metadata viewer role and hit add selected in the available roles.
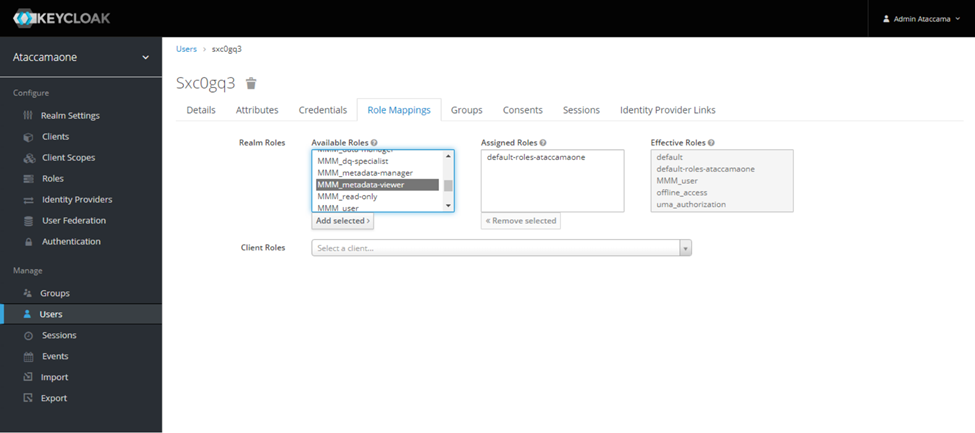
- After adding the role will be assigned to the user. When the user logs in to the ONE Web app he will not be able to view the data.
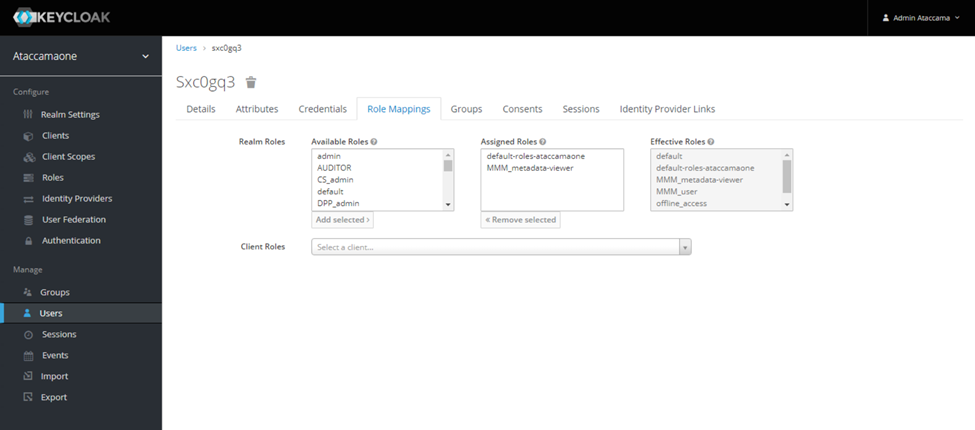
- When the user logs in to the ONE Web Application and tries to access data the data tab will show an error message.