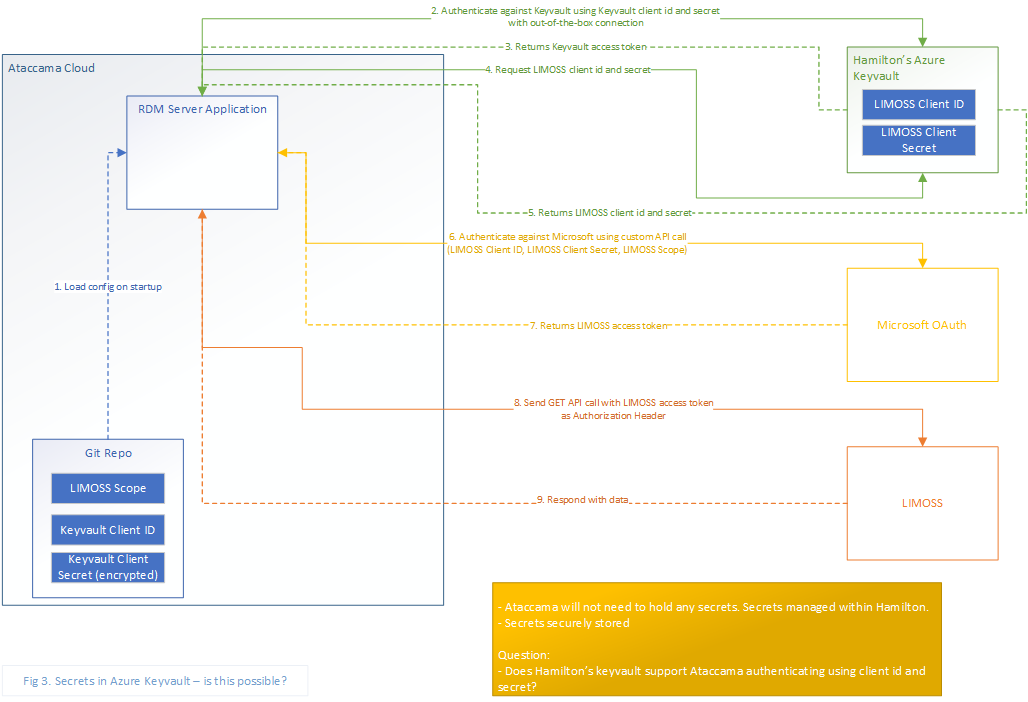
I have a use case where I want to store some client id and secret in my own company’s Azure keyvault.
Then I have a component which needs to use the client id and secret to authenticate against a 3rd party, so I can issue a GET call to get some data.
So I am thinking:
- Runtime server authenticate against keyvault
- Runtime server issue a “get secret” call to keyvault
- Keyvault sends back the secret
- Runtime server takes the secret and authenticate against 3rd party
- Runtime server issue a “get data” call to 3rd party
- 3rd party sends me back the actual data
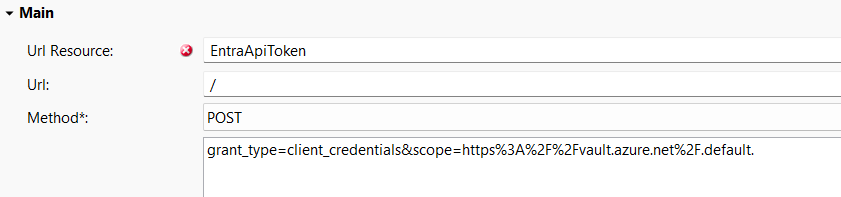
What authentication methods from runtime server to keyvault are supported? I had a look at Azure keyvault’s documentation but I don’t think I understand it fully. https://learn.microsoft.com/en-us/azure/key-vault/general/authentication
Has anybody else done it? What’s your experience?